The Turkish internet provider Türk Telekom uses Deep Packet Inspection to systematically manipulate downloads and to infect some users with malware. The same technology is used in Egypt to secretly redirect internet users to advertisements or to mine cryptocurrencies.
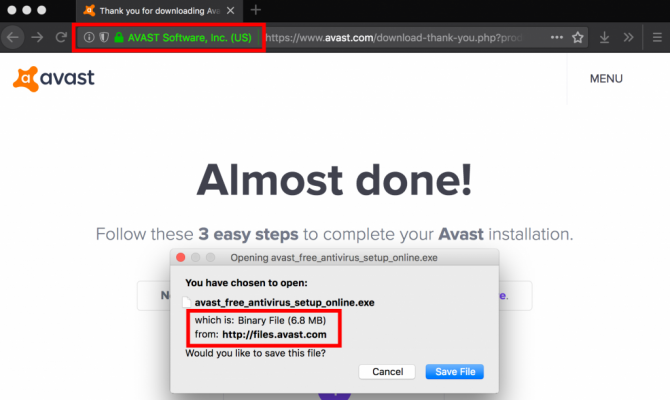
(Insecure download of Avast through unencrypted HTTP connection)
Security researchers from the Canadian organization Citizen Lab found that hundreds of users from Türk Telekom have been redirected to spyware infected versions of Avast, VLC, WinRar, Skype, 7-Zip, Opera or CCleaner. Although the official sites of the software used HTTPS, the actual file downloads were through unencrypted HTTP connections. Therefore, it was possible to perform a so-called Man-In-The-Middle(MITM) attack. In case of Türk Telekom, HTTP headers were injected which redirected users to spyware infected versions of the software.
Citizen Lab estimates that hundreds of IP addresses, especially around the Turkish-Syrian border have been affected. Users in war-torn Syria, often use Turkish Wi-Fi connections to connect to the internet. Turkey is currently fighting with Syrian Curds at its border which could be a motive for wanting to install spyware on computers.
The MITM attacks were discovered by Citizen Lab by scanning the Türk Telekom network. They found that there are servers in the network, called 'middle boxes' by Citizen Lab, that perform deep packet inspection (DPI) and that are used for the MITM attacks.
Similar servers were also found in the network of Egypt Telecom. However, the middle boxes on the Egypt Telecom network were not used to redirect users to spyware infected software. Instead, there were used to hijack loads of unencrypted connections of users on Egypt Telecom's network. Once the connection was hijacked, users were redirected to pages loaded with (affiliate) advertisements or crypto-mining scripts for a certain period.
After intensive investigation, Citizen Lab found that both occurrences of network injection relied on the same technology. All middle boxes used technology from the Canadian company Sandvine, which sells PacketLogic servers, that are specially designed to, “prioritize, degrade, block, inject, and log various types of Internet traffic.”
In 2014, a Turkish newspaper reported that the Turkey was in negotiations with Sandvine to purchase their equipment for internet surveillance and censorship. Citizen Lab found that it's indeed Sandvine PacketLogic servers that are currently employed to block political, journalistic and human rights content in both Turkey and Egypt. The blocked websites include Wikipedia, websites of several international human-rights organizations and several news sites. On LinkedIn, Citizen Lab also found that Sandvine had an engineer in Istanbul (a big city in Turkey), which made them wonder whether Sandvine actively participated in censoring the internet in Turkey.
When Citizen Lab shared its findings with SandVine, it received a reply that the findings were, “false, misleading, and wrong.”
The findings from Citizen Lab highlights the importance of HTTPS traffic. Encrypted traffic is not susceptible to MITM attacks which means it's not possible for attackers to redirect users to e.g. spyware infected downloads or to pages that only contain advertisements or abuse computer resources for crypto mining. Some software vendors have now switched to HTTPS downloads.
However, Citizen Lab remains concerned about human rights, although the companies that deliver DPI technology are likely in accordance with applicable laws, their technology can be abused by 'evil' states to censor information or to spy on its citizens.
















